| zurück
Home |
WinZip |
Allgemeines |
 |
Programme zur Kompression von Dateien und
Verzeichnissen. |
Modus |
Programm - Modus: Aufruf von WinZip unter Windows
oder Linux. |
Kommando - Modus: In BAT-Dateien kann eine Folge von
Zip- und Unzip-Aufträgen abgearbeitet werden. Hervorragend für Backup und
Transfer. Alleinstellungsmerkmal von WinZip! |
Integrierter Modus: Im Explorer lassen sich
ZIP-Daten öffnen, ohne das Programmfenster zu benutzen. Im WinCommander können
auch Daten kopiert , hinzugefügt oder gelöscht werden. Bei USB-Sticks gibt es
z.T. Probleme wegen des Speicherplatzes, weil WinZip bei Änderungen zunächst
eine 2. Zip-Datei erstellt und dann erst die alte Datei löscht (doppelter
Speicherbedarf). |
Programm - Start |
Nach dem Programmstart wird eine leere ZIP-Datei angezeigt.
 |
neue Datei |
Um ganze Verzeichnisse einzutragen, muss als
Dateiname z.B. *.* eingetragen sein. Dann kann mit "Add with wildcards" der
Eintrag gestartet werden. Bei geschachtelten Verzeichnissen "Include Subfolders"
nicht vergessen.
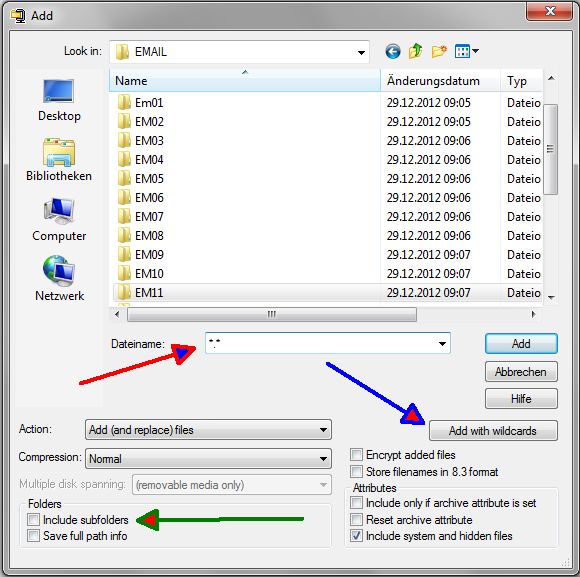 |
Installation |
Wenn man keine Lizenz besitzt, so macht WinZip bei
jedem Aufruf einen Hinweis, der bestätigt werden muss. Hat man eine Lizenz, so
sollte man die Produktnummer eingeben, bevor man die Kommandozeilenfunktion
installiert. Ansonsten bekommt man die lästige Meldung trotz freigeschalteter
Lizenz. |
| Kompression |
Batch-Befehle: -u Update, -rP kompletten Pfad
speichern, -t10.08.2011 Datumsschwelle |
Beispiel: WZzip -u -rp -t10.07.2012 -o Ziel.zip
d:\Quelle\*.* |
| Zeitfenster |
Unter den Komprimierungstools kann nur WINZIP Dateien in einem Zeitfenster selektieren. |
| Dekompression |
|
| Dateiliste |
Anstelle einzelner Dateien kann im Batch der Name
einer Dateiliste angegeben werden. |
WZzip -x@z_db.lst c:\\DBIV\*.*: z_db.lst enthält die
Dateien, die nicht gesichert werden sollen (-x) |
z_db.lst. Die Dateiliste ist eine einfache Textdatei
(Editor, nicht Word!!) mit der Endung .lst. Die Dateien werden zeilenweise
eingegeben. |
| Versionen |
- Winzip Version 21: 11/16
- Winzip Version 20.5: bis Win 8.1, 10,32- und 64 - Bit
- Winzip Version 19: Cloud-Unterstützung, bis Win 8.1, 32- und 64 - Bit
- Winzip Version 18
- Winzip Version 17.5: 2013, 128- und 256-Bit AES-Verschlüsselung, WinZip
Courier, Datenschutz in der Cloud
- Winzip Version 16.5: 2012
- WinZip Version 9.0: 2004
- WinZip 8.0: 2000
- WinZip 7.0: 1998
- WinZip 6.2: 1995
- WinZip 3.2: 1996
- Zip 93: 1993
- Zip 89: 1989
|
| verschlüsselter Transfer |
Mit Batchmode kann WinZip aktuelle Dateien
verschlüsselt auf einem USB-Stick sichern und übertragen. |
| Quellen |
1.) http://www.winzip.com
2.) http://www.winzip.de
3.) http://www.info-zip.org
kostenlose Infos und Downloadadressen
|
Teil von |
Packer, Kompression |
Utilities |
Software |
 |
About encryption and encryption methods Encryption gives you a way to
protect sensitive documents contained in your archives. The contents of the
files that you want to protect are encrypted by WinZip® Command Line Support
Add-On based on a password that you specify. In order to later extract the
original contents of the encrypted files, the correct password must again be
supplied. The WinZip Command Line Support Add-On provides two basic
encryption methods for Zip files: · AES encryption: AES is the Advanced
Encryption Standard, which is the result of a three-year competition
sponsored by the U.S. Government's National Institute of Standards (NIST).
This encryption method, also known as Rijndael, has been adopted by NIST as
a Federal Information Processing Standard. The add-on supports AES
encryption in two different strengths: 128-bit AES and 256-bit AES. These
numbers refer to the size of the encryption keys that are used to encrypt
the data. 256-bit AES is stronger than 128-bit AES, but both of them can
provide significantly greater security than the standard Zip 2.0 method
described below. An advantage of 128-bit AES is that it is slightly faster,
that is, it takes less time to encrypt or decrypt a file. The security of
your data depends not only on the strength of the encryption method but also
on the strength of your password, including factors such as length and
composition of the password, and the measures you take to ensure that your
password is not disclosed to unauthorized third parties. Please read about
encryption passwords. Note that the Zip file format extension used by the
WinZip Command Line Support Add-On to store AES-encrypted files is not
supported by earlier versions of WinZip and is not yet supported by most
other Zip file utilities. Because the technical specification for WinZip's
AES format extension is available on the WinZip web site, we anticipate that
other Zip file utilities will add support for this format extension. ·
Standard Zip 2.0 encryption: this older encryption technique provides a
measure of protection against casual users who do not have the password and
are trying to determine the contents of the files. However, the Zip 2.0
encryption format is known to be relatively weak, and cannot be expected to
provide protection from individuals with access to specialized password
recovery tools. You should not rely on Zip 2.0 encryption to provide strong
security for your data. If you have important security requirements for your
data, you should use WinZip's AES encryption, described above. The only
advantage of Zip 2.0 encryption over the more secure AES encryption is that
it is supported by most Zip file utilities, including earlier versions of
WinZip. Files that you encrypt using this technique can be extracted by
anyone who knows the correct password and has access to almost any Zip file
utility. Some points to be aware of: · Encryption applies only to the
contents of files stored within a Zip file. Information about an encrypted
file, such as its name, date, size, attributes, and compression ratio, is
stored in unencrypted form in the Zip file's directory and can be viewed,
without a password, by anyone who has access to the Zip file. · The correct
password must be specified before the contents of an encrypted file within a
Zip file can be viewed or accessed in unencrypted form. The password is not
required, however, for actions that do not require access to the unencrypted
contents of the file. In particular, encrypted files can be deleted from a
Zip file, or can be replaced within the Zip file, without a password. Please
read about using encryption. Notes on encryption safety Encryption provides
a measure of safety for your sensitive documents, but even encrypted
documents can be compromised (regardless of whether they were encrypted by
the WinZip Command Line Support Add-On or by other encryption software).
Here are some of the ways this can occur. This is by no means an exhaustive
list of potential risks; it is intended only to give you an idea of some of
the safety issues involved with sensitive documents. · If a keystroke
monitor or other malicious code (such as a virus) is running on your
computer, your password may be recorded when you type it. Be sure to check
frequently for viruses and follow other recommended computer safety
procedures. · If you extract an encrypted file and then delete the file, it
may be possible for someone to later "undelete" the file using file recovery
software or the Recycle Bin. · When you open or view a decrypted file, the
associated program may make one or more backup copies of the decrypted file.
· When you "move" files to a Zip file by choosing the Move command, the
add-on moves the files into the Zip file by compressing them and then
deleting the original files from the disk. It may be possible to recover the
original, unencrypted files from the disk. · After encrypting files, some or
all of the unencrypted file contents may remain in your computer's memory or
the page swap files on disk. A malicious user may be able to retrieve this
unencrypted information from memory. · As described above, the add-on does
not encrypt information about encrypted files such as their names, dates,
etc. Any user with access to the Zip file can view this information without
a password. You may be able to eliminate some of these exposures using
specialized software such as virus scanners, disk erasers, etc. Technical
information on AES key generation When you use AES encryption with WinZip,
the passwords that you enter are converted into keys of the appropriate
length (128 bits or 256 bits, depending on the AES key length that you
specify). This is done through the PBKDF2 algorithm defined in RFC 2898
(also available as Public Key Cryptography Standard #5) with an iteration
count of 1000. 8-byte salt values are used with 128-bit AES encryption and
16-byte salt values are used with 256-bit encryption. As part of the process
outlined in RFC 2898 a pseudorandom function must be called; WinZip uses the
HMAC-SHA-1 function for this purpose, since it is a well-respected algorithm
that has been in wide use for this purpose for several years. The PBKDF2
function repeatedly calls HMAC-SHA-1, which produces a 160-bit hash value as
a result, mixing the outputs in a fairly complicated way, eventually
yielding a 128- or 256-bit encryption key as a result. Note that, if you are
using 256-bit AES encryption, the fact that HMAC-SHA-1 produces a 160-bit
result means that regardless of the password that you specify, the search
space for the encryption key is unlikely to reach the theoretical 256-bit
maximum, and cannot be guaranteed to exceed 160 bits. This is discussed in
section B.1.1 of the RFC 2898 document. Information for software developers
Zip file utility developers who wish to provide WinZip-compatible AES
encryption support in their own products can find complete technical
information at http://www.winzip.com/aes_info.htm. See also: Using
Encryption The -s command enables encryption. By default, Zip 2.0 encryption
is used. By specifying the -yc command after the -s command, the encryption
method can be changed to one of the WinZip AES encryption methods. Examples:
wzzip sample.zip -spassword *.txt All files with a .txt extension are added
to the Zip file "sample.zip". The files are encrypted with Zip 2.0
encryption. They are encrypted using the specified password "password".
wzzip sample.zip -s -yc *.txt All files with a .txt extension are added to
the Zip file "sample.zip". The files are encrypted using WinZip's 128-bit
AES encryption. A prompt will be generated requesting the password. wzzip
sample.zip -s -ycAES256 *.txt All files with a .txt extension are added to
the Zip file "sample.zip". The files are encrypted using WinZip's 256-bit
AES encryption. A prompt will be generated requesting the password. Notes on
using encryption The security of your data depends not only on the strength
of the encryption method but also on the strength of your password,
including factors such as length and composition of the password, and the
measures you take to ensure that your password is not disclosed to
unauthorized third parties. You should keep the following considerations in
mind when choosing passwords for your files: · In general, longer passwords
are more secure than shorter passwords. In fact, taking maximum advantage of
the full strength of AES encryption requires a password of approximately 32
characters for 128-bit encryption and 64 characters for 256-bit encryption.
· Passwords that contain a mixture of letters (upper and lower case),
digits, and punctuation are more secure than passwords containing only
letters. · Because you can use spaces and punctuation, you can create "pass
phrases" that are long enough but still easy to remember and type. · Avoid
using easily guessed passwords such as names, birthdays, Social Security
numbers, addresses, telephone numbers, etc. Be sure to keep a record of the
passwords you use and to keep this record in a secure place. The WinZip®
Command Line Support Add-On has no way to access the contents of an
encrypted file unless you supply the correct password. Copyright © 2004
WinZip Computing, Inc. All rights reserved. Copyright © 2004 WinZip
Computing, Inc. All rights reserved.


